As we navigate through early 2026, the concept of being “too small to target” has become a dangerous myth that has led to the downfall of countless small enterprises. Cybercriminals have industrialized their operations. They no longer rely on manual hacking; instead, they are deploying autonomous “Agentic AI” swarms that scan the internet 24/7, looking for unpatched routers, weak passwords, and misconfigured cloud servers.
For a small business owner today, the stakes have never been higher. A single breach now costs an average of $200,000 in ransomware payments, legal fees, and lost revenue—enough to bankrupt 60% of small businesses within six months of an attack. But here is the good news: 98% of these attacks are preventable with the right hygiene and architecture.
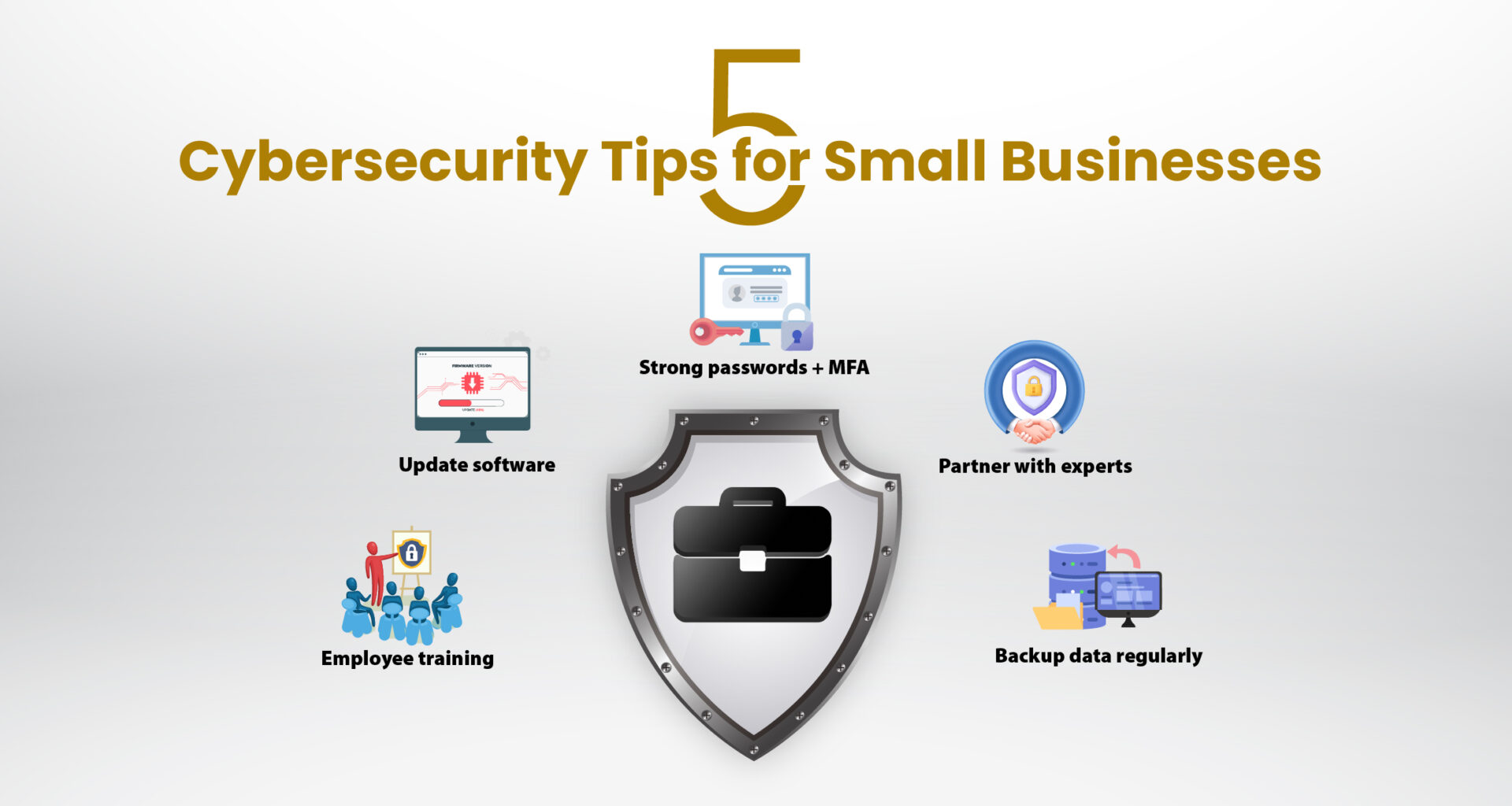
This is not a generic list of tips. This is a comprehensive masterclass on building a digital fortress. We will cover everything from hardware defenses to the psychology of your employees, ensuring your business remains resilient in the face of today’s AI-driven threats.
Table of Contents
- 1. The 2026 Threat Landscape: Agentic AI & RaaS
- 2. Identity Access: Killing the Password
- 3. The 3-2-1-1 Immutable Backup Architecture
- 4. Zero Trust & Network Segmentation
- 5. Building the Human Firewall
- 6. The “First Hour” Incident Response Protocol
- 7. Budgeting for Security: Protection Under $500
- 8. Frequently Asked Questions (FAQ)
- 9. Conclusion
1. The 2026 Threat Landscape: Agentic AI & RaaS
To defeat your enemy, you must first understand them. This year, we are witnessing the convergence of two terrifying trends: Ransomware-as-a-Service (RaaS) and Agentic AI.
What is Agentic AI?
Unlike traditional bots that just run a script, Agentic AI agents are autonomous. They can reason, adapt, and make decisions. If an AI agent encounters a firewall, it doesn’t just stop; it tries a different method, such as searching for your employee’s credentials on the dark web or crafting a personalized phishing email to your receptionist.
To understand the mechanics of these sophisticated tools, we highly recommend reading our detailed analysis on the functions and types of AI agents. Knowing how these autonomous systems operate is the first step in designing a defense that can withstand them.
The Reality of “Quintuple Extortion”
Ransomware is no longer just about encrypting your files. Attackers are currently applying five layers of pressure:
- Encryption: Locking your files.
- Theft: Stealing sensitive customer data.
- Denial of Service (DDoS): Crashing your website until you pay.
- Harassment: Calling your customers to tell them you’ve been hacked.
- Short Selling: Betting against your company’s stock (if public) or reputation.
2. Identity Access: Killing the Password
The traditional password is the single greatest liability in your security architecture. In an era where AI can crack an 8-character password in milliseconds, relying on memory-based secrets is negligent.
The New Standard: FIDO2 Hardware Keys
We strongly advocate for moving to a Passwordless environment using FIDO2 hardware keys. These are physical USB or NFC devices that you must touch to log in. They are immune to phishing because even if an employee enters their credentials into a fake website, the login will fail without the physical key.
Comparison: YubiKey vs. Google Titan
Choosing the right key depends on your ecosystem. Here is a breakdown:
| Feature | YubiKey 5 Series | Google Titan Key |
|---|---|---|
| Protocol Support | FIDO2, U2F, Smart Card, OTP, OpenPGP | FIDO2, U2F |
| Durability | IP68 Rated (Water & Dust Proof), Crush Resistant | Standard Build Quality |
| Cost | $50 – $75 USD | $30 – $40 USD |
| Best For | Enterprises requiring versatile protocols | Small businesses using Google Workspace |
Adopting these physical tokens is a prime example of how cybersecurity is getting stronger. By removing the human element (memory) from the equation, we eliminate the most common point of failure.
3. The 3-2-1-1 Immutable Backup Architecture
If you take only one thing from this guide, let it be this: Backups are your only defense against paying a ransom. However, standard backups are no longer enough because modern ransomware creates a “sleeper” infection that corrupts your backups over weeks before locking your system.
The Strategy Explained
- 3 Copies of Data: You need the original data plus two copies.
- 2 Different Media Types: Do not keep everything on the same hard drive. Use a mix of NAS (Network Attached Storage) and Cloud.
- 1 Offsite Copy: In case of a physical fire or flood at your office.
- 1 Immutable Copy (The Golden Rule): This is a backup that is locked with a “WORM” (Write Once, Read Many) policy. It cannot be deleted, encrypted, or modified for a set period (e.g., 30 days)—not even by the CEO or the IT Administrator.
Implementation Guide
Modern cloud providers like AWS S3, Wasabi, or Backblaze B2 offer “Object Lock” features. You should configure your backup software to send encrypted data to these buckets. Leveraging AI tools that change modern workflows, you can automate this entire process. An AI-driven backup solution can detect anomalies—such as a sudden mass-encryption of files—and halt the backup process to prevent your clean backups from being overwritten by corrupted data.
4. Zero Trust & Network Segmentation
The old model of security was like a castle: a strong wall (Firewall) on the outside, but wide open on the inside. Once a hacker breached the wall, they could move anywhere. The new model, Zero Trust, assumes the hacker is already inside.
Why Network Segmentation Matters
Your office is filled with “dumb” devices. Smart fridges, connected printers, and even smart lightbulbs often lack basic security features. If these devices are on the same network as your payroll computer, a hacker can enter through the lightbulb and steal your bank details. This is known as “Lateral Movement.”
Step-by-Step Guide: Configuring Your Router
You don’t need an expensive enterprise firewall to fix this. Most modern business routers (like ASUS, Ubiquiti, or TP-Link) support VLANs (Virtual Local Area Networks) or Guest Networks.
- Access Admin Panel: Usually accessible via
192.168.1.1or192.168.0.1in your browser. - Create a Guest Network: Label it
Office_IoT_Devices. - Enable Isolation: Look for a setting called “AP Isolation” or “Device Isolation.” This prevents devices on this network from talking to each other.
- Migrate Devices: Move all printers, smart TVs, and employee personal phones to this Guest Network.
- Secure the Core: Only company-issued, secured laptops should remain on the main network.
These devices are constantly collecting data. As we’ve explored in our article on how smart devices learn from your environment, leaving them unsecured is a privacy nightmare waiting to happen.
5. Building the Human Firewall
You can buy the most expensive firewall in the world, but if your accountant clicks on a malicious link, you are compromised. Social engineering now utilizes “Deepfakes”—AI-generated audio and video that mimic real people.
The “Challenge Phrase” Protocol
Establish a verbal password system for your executives and finance team. If the CEO calls the CFO and asks for an urgent wire transfer, the CFO must ask: “What is the challenge phrase?” If the caller (even if it sounds exactly like the CEO) cannot answer, it is a deepfake.
Gamified Training
Stop doing boring annual seminars. Use phishing simulation tools that send fake “scam” emails to your employees at random times. If they click, they are redirected to a micro-learning module. This keeps security top-of-mind. Remember, technology is shaping human evolution, and our natural instinct to trust must be retrained for a digital environment where “seeing is believing” no longer applies.
6. The “First Hour” Incident Response Protocol
When a breach occurs, panic causes more damage than the malware. You need a “Digital Fire Drill.” Here is what to do in the first 60 minutes of a suspected attack.
🚨 INCIDENT RESPONSE CHECKLIST
- Step 1: Isolate (0-10 Mins): Do NOT turn off the infected machine (you lose evidence). Instead, unplug the Ethernet cable or disable Wi-Fi. Disconnect backup drives immediately.
- Step 2: Verify (10-20 Mins): Confirm it is a real attack. Take photos of the screen with a mobile phone. Do not open files or run antivirus scans yet (this can trigger ransomware logic).
- Step 3: Mobilize (20-30 Mins): Call your Cyber Insurance provider. They will assign a “Breach Coach” and legal counsel.
- Step 4: Contain (30-60 Mins): Reset all passwords for all users (Admin first). Enable “Lockdown Mode” on your firewall if available.
Effective communication is vital. You must protect your reputation while adhering to regulations regarding protecting personal data privacy. Transparency builds trust; hiding a breach destroys it.
7. Budgeting for Security: Protection Under $500
Many small business owners think security requires an Enterprise budget. That is false. Here is how you can secure a 5-person team for under $500 upfront.
- Password Manager (Bitwarden): Free for basic business use.
- Hardware Keys (YubiKey Security Key NFC): $25 per key x 5 employees = $125.
- DNS Filtering (Cloudflare Gateway): Free tier protects against malicious sites.
- Encrypted Backups (Wasabi/Backblaze): Approx $6/TB per month.
- Endpoint Protection (Windows Defender for Business): Included in Microsoft 365 Business Premium subscriptions.
For remote teams, ensuring their home setup is secure is also part of this budget. Check out the latest trends in remote work technology to see how affordable tools are bridging the security gap.
8. Frequently Asked Questions (FAQ)
Q: Do I really need an antivirus if I have a Mac?
A: Yes. While Macs are more secure than Windows by default, Mac-targeted malware increased by 400% in 2025. You need an EDR (Endpoint Detection and Response) tool regardless of OS.
Q: Is Cloud storage considered a backup?
A: Google Drive or OneDrive is syncing, not backing up. If you delete a file on your PC, it deletes in the cloud. You need a dedicated backup service that keeps historical versions.
Q: How often should we test our backups?
A: At least once a month. A backup that hasn’t been tested is just a wish.
Q: What is the biggest security risk right now?
A: It remains the human element. Deepfake social engineering and phishing account for over 80% of initial breaches.
9. Conclusion
Building digital resilience is not a destination; it is a journey. The threats of 2026—Agentic AI, deepfakes, and automated ransomware—are formidable, but they are not unbeatable.
By implementing the strategies outlined in this handbook—shifting to hardware-based identity, automating immutable backups, and segmenting your network—you are doing more than just securing data. You are securing the future of your business.